kubernetes环境jenkinsCI—CD配置文档
jenkins CI/CD 配置文档
1.全局工具配置
1.1 maven配置
默认 settings 提供
文件路径:/usr/local/bin/apache-maven-3.3.9/conf/settings.xml
默认全局 settings 提供
文件路径 :/usr/local/bin/apache-maven-3.3.9/conf/settings.xml
1.2 jdk
别名:jdk8
JAVA_HOME :/usr/local/openjdk-8
1.3 git
Name :Default
Path to Git executable :/usr/bin/git
1.4 maven
name :maven
MAVEN_HOME : /usr/local/bin/apache-maven-3.3.9
2.下载kubernetes 插件
2.1 kubernetes plugin 安装
首先进入插件管理页面【系统管理】->【管理插件】->【可选插件】,搜索kubernetes plugin,勾选要安装的插件,然后点击【直接安装】。
2.2 配置kubernetes
单击【系统管理】 - >【系统设置】,找到【云】,然后点击【新增一个云】
WX20200102-151850.png
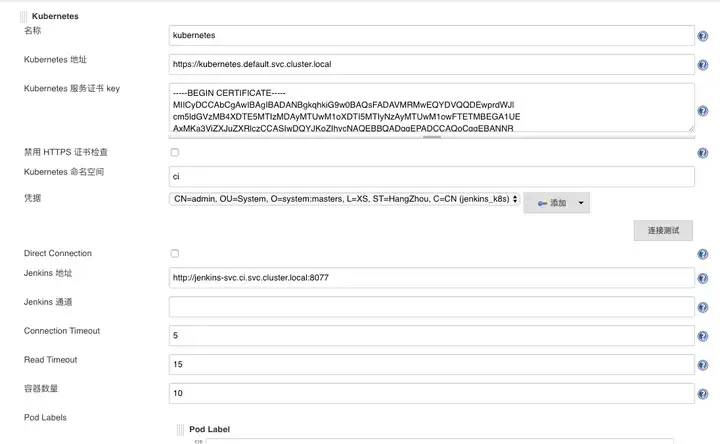
name:kubernetes
禁用https证书检查:false
kubernetes URL:https://kubernetes.default.svc.cluster.local
Kubernetes 服务证书 key : 为k8s集群生成的ca证书
cat /etc/kubernetes/pki/ca.crtJenkinsURL:http://jenkins-svc.ci.svc.cluster.local:8077(服务名.命名空间.svc.cluster.local:端口)
连接超时:5
读取超时:15
凭据:根据下面命令获取
1.直接使用二进制源码包安装cfssl
wget https://pkg.cfssl.org/R1.2/cfssl_linux-amd64
chmod +x cfssl_linux-amd64
mv cfssl_linux-amd64 /usr/local/bin/cfssl
wget https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64
chmod +x cfssljson_linux-amd64
mv cfssljson_linux-amd64 /usr/local/bin/cfssljson
wget https://pkg.cfssl.org/R1.2/cfssl-certinfo_linux-amd64
chmod +x cfssl-certinfo_linux-amd64
mv cfssl-certinfo_linux-amd64 /usr/local/bin/cfssl-certinfo
export PATH=/usr/local/bin:$PATH
准备证书签名请求
mkdir /usr/local/k8s/cfssl
cd /usr/local/k8s/cfssl
vi admin-csr.json
{
"CN": "admin",
"hosts": [],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "HangZhou",
"L": "XS",
"O": "system:masters",
"OU": "System"
}
]
}
3.创建证书和私钥
cd /usr/local/k8s/cfssl
cfssl gencert -ca=/etc/kubernetes/pki/ca.crt -ca-key=/etc/kubernetes/pki/ca.key --profile=kubernetes admin-csr.json | cfssljson -bare admin
生成以下三个文件
ls -l
admin.csr
admin-key.pem
admin.pem
4.我们可以通过openssl来转换成pkc格式:
openssl pkcs12 -export -out ./jenkins-admin.pfx -inkey ./admin-key.pem -in ./admin.pem -passout pass:secret
生成jenkins-admin.pfxpfx文件
ls
jenkins-admin.pfx下载jenkins-admin.pfx到本地保存
将证书内容填写,点击凭据后面的添加,点击Jenkins
得到jenkins-admin.pfk文件后,点击Jenkins配置Credentials后面的Add,配置如下
上传证书
1341090-20190812121333313-1393693991.png
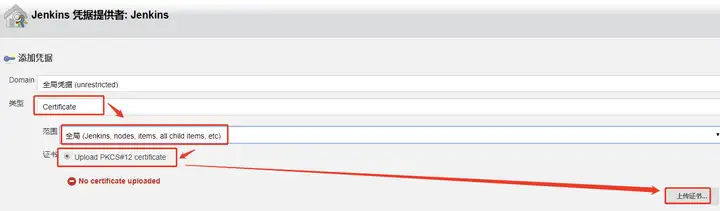
选择文件 jenkins-admin.pfk
22.png
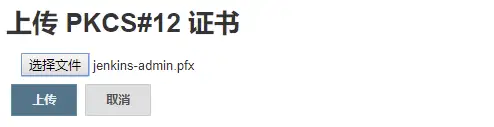
输入密码 secret,后面的内容可以不填写,点击添加。
33.png
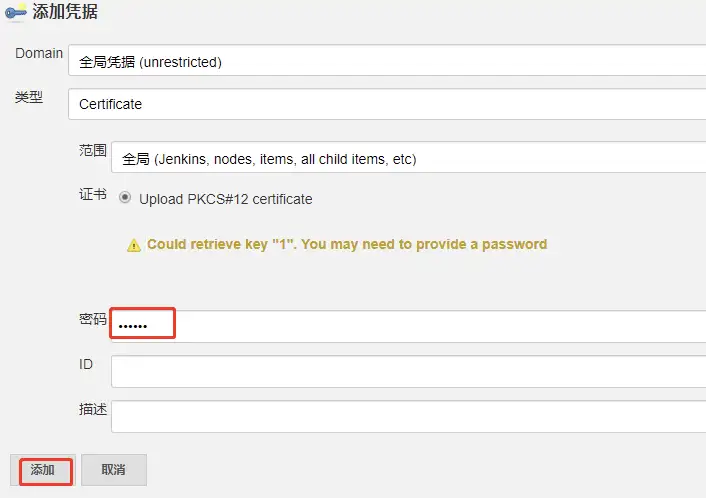
选择 凭据,点击连接测试。
出现 Connection test successful 表示连接成功。
2.3配置 Pod Template
构建slave镜像
docker pull cnych/jenkins:jnlp6
docker tag cnych/jenkins:jnlp6 harbor.demo.com/private/demo-jenkins:jnlp
docker push harbor.demo.com/private/demo-jenkins:jnlp设置Pod Template ( jenkinsfile 中label标签和标签列表设置保持一致)
WX20200102-154511.png
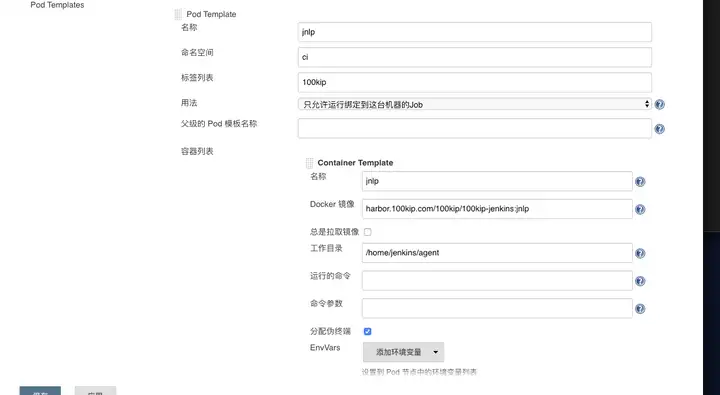
添加卷 WX20200102-154721.png
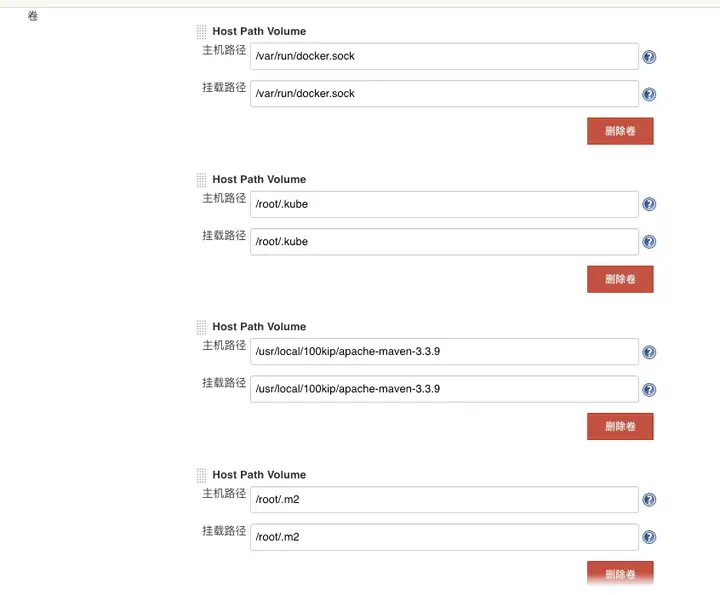
Service Account:jenkins
3.gitlab 设置
下载gitlab插件
系统管理—系统配置-Gitlab
WX20200102-155116.png
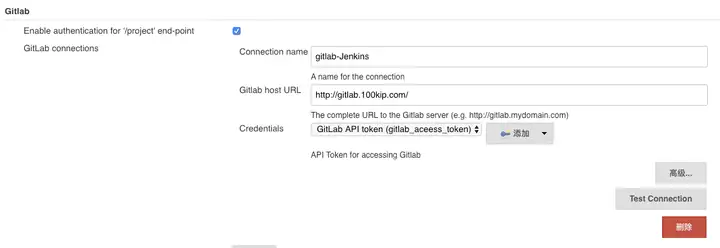
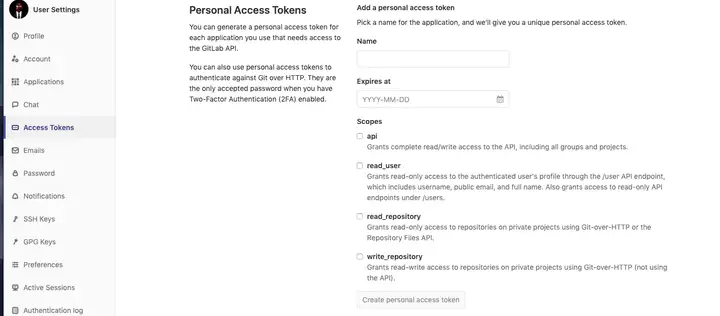
GitLab API token API token 在gitlab-settings-Access Token获取
WX20200102-155245.png
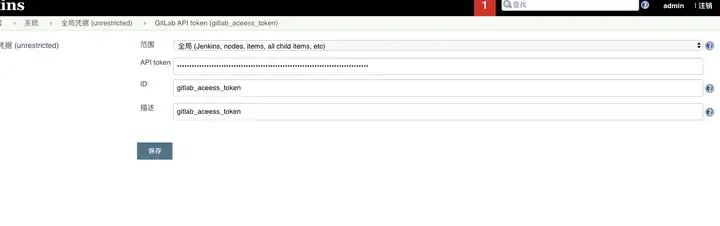
WX20200102-155641.png
4.新建pipeline任务
podTemplate(label: 100kip, cloud: kubernetes) {
node(100kip) {
environment {
harborHost = ""
harborCertificate = ""
kubeconfigId = ""
privateHarbor = ""
version=""
images=""
yamlPath="";
}
stage(Clone) {
echo "1.Clone Stage"
checkout([$class: GitSCM,
branches: [[name: */${branch}]],
doGenerateSubmoduleConfigurations: false,
extensions: [[$class: CloneOption, depth: 1, honorRefspec: true, noTags: true, reference: , shallow: true]],
submoduleCfg: [],
userRemoteConfigs: [[credentialsId: jenkins_gitlab, url: ${git_url}]]]
)
}
stage(pom version) {
echo "2.pom version"
def pom = readMavenPom file: pom.xml
version = "${pom.version}"
harborHost = "harbor.demo.com"
harborCertificate = "harbor_username_password"
kubeconfigId = "kubernetes_config"
privateHarbor = "${harborHost}\\/kb"
images = "${privateHarbor}\\/${module}:${version}-${BUILD_NUMBER}"
echo "version:${version}-----privateHarbor:${privateHarbor}----images:${images}"
def isCanary="${canary}";
if(isCanary == "true"){
echo "灰度发布"
yamlPath = "k8s/${profiles}/canary/${module}-canary.yaml";
}else{
yamlPath = "k8s/${profiles}/${module}.yaml";
}
}
stage(Maven bulid) {
echo "2.Maven bulid"
sh "mvn clean package -pl ${module} -P ${profiles} -DskipTests -U "
}
stage(Docker build) {
echo "3.Build Docker Image Stage"
def buildArg = "-f ${module}/Dockerfile --build-arg version=${version} --build-arg module=${module} ."
def customImage = docker.build("${images}", "${buildArg}")
docker.withRegistry("http://${harborHost}", "${harborCertificate}") {
customImage.push()
}
}
stage(K8S Deploy) {
echo "K8S Deploy"
sh "sed -i s/${module}:lastest/${images}/g ${yamlPath}"
kubernetesDeploy configs: "${yamlPath}", kubeconfigId: "${kubeconfigId}"
echo "Service deploy successfully! please request http://${domain}"
}
}
}本文由博客群发一文多发等运营工具平台OpenWrite发布
配置好源码管理之后可以直接先保存构建一次
下面这个能跑通的前提是用户已经打通Credentials
Jenkins发布PHP项目之一自动化部署
这个说白了就是拉取到上线文件之后,直接通过执行rsync命令,来实现发布到对应的服务器

