如何生成Letsencrypt免费单个域名ssl证书
访问网站使用https协议加密传输,更安全。给网站启用
访问网站使用https协议加密传输,更安全。给网站启用https,首先要有https的ssl证书。 以前,ssl证书几乎都是要向第三方购买的,直到Lets encrypt提供签证免费的ssl证书,少延终于用上了https。 下文,实操一波,给单个域名生成Lets encrypt免费ssl证书。证书只有3个月有效期,但是没关系,可以配置自动续期。预祝有需要的小伙伴,早点用https。
1.环境说明
阿里云主机
系统版本:CentOS Linux release 7.6.1810 (Core)
2.安装依赖和工具
[root@sy-ali-vps:~]cat /etc/redhat-releaseCentOS Linux release 7.6.1810(Core)打开 https://certbot.eff.org/ 选择对应版本。我这里是nginx + centos7[root@sy-ali-vps:~]yum -y install yum-utils 按照依赖[root@sy-ali-vps:~]yum-config-manager --enable rhui-REGION-rhel-server-extras rhui-REGION-rhel-server-optional[root@sy-ali-vps:~]yum install python2-certbot-nginx 安装插件3.生成证书:
方法一: 配置 nginx 插件,并生成证书。这两参数知道配置路径及nginx命令路径
certbot --nginx-server-root /usr/local/nginx/conf --nginx-ctl /usr/local/nginx/sbin/nginx方法二:指定域名网站目录,生成证书
certbot certonly --webroot -w /data/www/chopper/frontend/public方法三:服务器没有跑web服务,也是可以生成的。这种方法工具会启动自带的web服务,如果80被占用了,命令会失败
certbot certonly --standalone不管哪个方法,刚开始的时候,都会要填一个邮箱接收通知,以及同意协议。这里使用第二种方法。也建议使用这种。 第一种,会操作服务的nginx,第三种会启用工具自带的web服务,要是服务器本身运行了nginx,那会造成端口冲突。
下面使用方法二生成证书。首先,域名要解析到服务器。 执行命令遇到报错
[root@sy-ali-vps:~]certbot certonly --webroot -w /data/www/test.shaoyan.pro/ImportError: No module namedrequests.packages.urllib3‘解决办法:pip install --upgrade --force-reinstallrequests==2.6.0urllib3重试
certbot certonly --webroot -w /data/www/test.shaoyan.pro/
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator webroot, Installer None
Enter email address(usedforurgent renewal and security notices)(Entercto
cancel): admin@shaoyan.pro
Starting new HTTPS connection(1): acme-v02.api.letsencrypt.org
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Pleasereadthe Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server at
https://acme-v02.api.letsencrypt.org/directory
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -(A)gree/(C)ancel: A
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing to share your email address with the Electronic Frontier
Foundation, a founding partner of the Lets Encrypt project and the non-profitorganization that develops Certbot? Wed like to send you email about our work
encrypting the web, EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -(Y)es/(N)o: Y
Starting new HTTPS connection(1): supporters.eff.org
Please enter in your domain name(s)(comma and/or space separated)(Entercto cancel): test.shaoyan.pro
Obtaining a new certificate
Performing the following challenges:
http-01 challengefortest.shaoyan.pro
Using the webroot path /data/www/test.shaoyan.proforall unmatched domains.
Waitingforverification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/test.shaoyan.pro/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/test.shaoyan.pro/privkey.pem
Your cert will expire on 2019-12-19. To obtain a new or tweaked
version of this certificate in the future, simply run certbot
again. To non-interactively renew *all* of your certificates, run"certbot renew"- Your account credentials have been saved in your Certbot
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Certbot so
making regular backups of this folder is ideal.
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Lets Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le[root@sy-ali-vps:~]证书生成成功。
4.添加自动更新ssl服务
通过方法一,也就是安装web 服务插件,只需要执行certbot renew即可,这个命令,会检测证书是否过期,并通过web 服务插件重载配置。 这里用的步骤2的方法二,所以呢要加 nginx 的重载配置命令,使用脚本更新证书:
!/usr/bin/env bash
certbot renew
/usr/local/nginx/sbin/nginx -s reload添加定时任务:
每天检查域名ssl证书是否过期,默认是到期前30天更新
0 1 * * * /data/sh/renew_ssl.sh >>/data/logs/crontab/renew_ssl.log 2>&1说明:
ls /etc/letsencrypt/
accounts archive csr keys live options-ssl-nginx.conf renewal renewal-hooks ssl-dhparams.pem生成的证书存了 archive 目录,live目录里面文件软连接到了archive。renewal 目录,存放了可以更新的域名,并且每个域名还可以配置更新规则。
如下是其中一个域名的更新配置。默认是有效期小于30天,进行更新证书。定时任务可以每天、或者每周执行一次。
[root@sy-ali-vps:/etc/letsencrypt/renewal] cat test.shaoyan.pro.conf
renew_before_expiry = 30 days
version = 0.37.2
archive_dir = /etc/letsencrypt/archive/test.shaoyan.pro
cert = /etc/letsencrypt/live/test.shaoyan.pro/cert.pem
privkey = /etc/letsencrypt/live/test.shaoyan.pro/privkey.pem
chain = /etc/letsencrypt/live/test.shaoyan.pro/chain.pem
fullchain = /etc/letsencrypt/live/test.shaoyan.pro/fullchain.pem
Options used in the renewal process
[renewalparams]
authenticator = webroot
account = dda3de758c33b839547c138955dfa763
webroot_path = /data/www/test.shaoyan.pro,
server = https://acme-v02.api.letsencrypt.org/directory
[[webroot_map]]
test.shaoyan.pro = /data/www/test.shaoyan.pro5.配置nginx
配置如下。吧80端口的访问,重定向到https
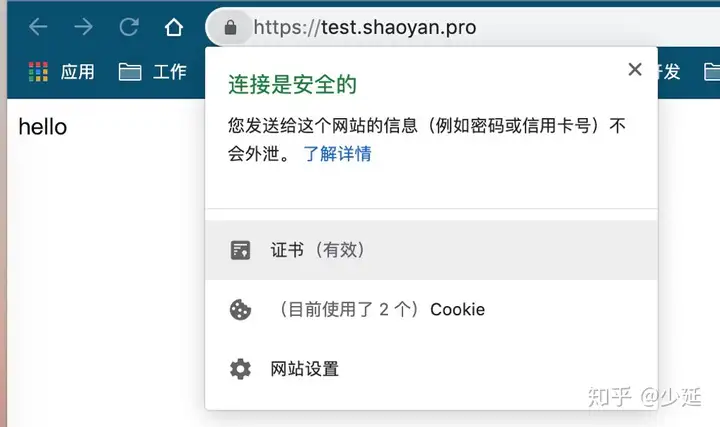
[root@sy-ali-vps:/etc/nginx/conf.d]cat test.shaoyao.pro.confserver{listen 80;server_name test.shaoyan.pro;root /data/www/test.shaoyan.pro;location /{rewrite ^/(.*)$ https://test.shaoyan.pro/$1permanent;}index index.html;}server{listen 443;ssl on;server_name test.shaoyan.pro;index index.html index.php;root /data/www/test.shaoyan.pro/public/;access_log /data/logs/www/nginx/test.shaoyan.pro_access.log;error_log /data/logs/www/nginx/test.shaoyan.pro_error.log;ssl_certificate /etc/letsencrypt/live/test.shaoyan.pro/fullchain.pem;ssl_certificate_key /etc/letsencrypt/live/test.shaoyan.pro/privkey.pem;ssl_session_timeout 5m;ssl_protocols TLSv1 TLSv1.1 TLSv1.2;ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:HIGH:!aNULL:!MD5:!RC4:!DHE;ssl_prefer_server_ciphers on;}[root@sy-ali-vps:/etc/nginx/conf.d]访问验证: